Fix broken links referencing to API docs (#14565)
* Fix all '/api/' to '/api-docs/' * Minor fixes * Undo some of the unintentional changes
This commit is contained in:
parent
08ea5f6d0a
commit
f374938d31
|
|
@ -48,13 +48,13 @@ parameters unset in your configuration.
|
|||
|
||||
- `region` `(string: "us-east-1")` - The region to use for signing the authentication request. The
|
||||
region Agent uses should match that corresponding to
|
||||
[`sts_endpoint`](/api/auth/aws#sts_endpoint),
|
||||
[`sts_endpoint`](/api-docs/auth/aws#sts_endpoint),
|
||||
if a custom endpoint has been configured on the Vault server.
|
||||
|
||||
- `session_token` `(string: optional)` - The session token to use for authentication, if needed.
|
||||
|
||||
- `header_value` `(string: optional)` - If configured in Vault, the value to use for
|
||||
[`iam_server_id_header_value`](/api/auth/aws#iam_server_id_header_value).
|
||||
[`iam_server_id_header_value`](/api-docs/auth/aws#iam_server_id_header_value).
|
||||
|
||||
- `nonce` `(string: optional)` - If not provided, Vault will generate a new UUID every time `vault agent` runs.
|
||||
If set, make sure you understand the importance of generating a good, unique `nonce` and protecting it.
|
||||
|
|
|
|||
|
|
@ -91,4 +91,4 @@ block.
|
|||
## API
|
||||
|
||||
Audit devices also have a full HTTP API. Please see the [Audit device API
|
||||
docs](/api/system/audit) for more details.
|
||||
docs](/api-docs/system/audit) for more details.
|
||||
|
|
|
|||
|
|
@ -108,5 +108,5 @@ can be found found in the
|
|||
## API
|
||||
|
||||
The AliCloud auth method has a full HTTP API. Please see the
|
||||
[AliCloud Auth API](/api/auth/alicloud) for more
|
||||
[AliCloud Auth API](/api-docs/auth/alicloud) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -120,5 +120,5 @@ management tool.
|
|||
## API
|
||||
|
||||
The AppID auth method has a full HTTP API. Please see the
|
||||
[AppID auth method API](/api/auth/app-id) for more
|
||||
[AppID auth method API](/api-docs/auth/app-id) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -240,7 +240,7 @@ guide for a step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The AppRole auth method has a full HTTP API. Please see the
|
||||
[AppRole API](/api/auth/approle) for more
|
||||
[AppRole API](/api-docs/auth/approle) for more
|
||||
details.
|
||||
|
||||
## Code Example
|
||||
|
|
@ -261,7 +261,7 @@ import (
|
|||
"os"
|
||||
|
||||
vault "github.com/hashicorp/vault/api"
|
||||
auth "github.com/hashicorp/vault/api/auth/approle"
|
||||
auth "github.com/hashicorp/vault/api-docs/auth/approle"
|
||||
)
|
||||
|
||||
// Fetches a key-value secret (kv-v2) after authenticating via AppRole.
|
||||
|
|
|
|||
|
|
@ -742,7 +742,7 @@ The response will be in JSON. For example:
|
|||
## API
|
||||
|
||||
The AWS auth method has a full HTTP API. Please see the
|
||||
[AWS Auth API](/api/auth/aws) for more
|
||||
[AWS Auth API](/api-docs/auth/aws) for more
|
||||
details.
|
||||
|
||||
## Code Example
|
||||
|
|
@ -761,7 +761,7 @@ import (
|
|||
"fmt"
|
||||
|
||||
vault "github.com/hashicorp/vault/api"
|
||||
auth "github.com/hashicorp/vault/api/auth/aws"
|
||||
auth "github.com/hashicorp/vault/api-docs/auth/aws"
|
||||
)
|
||||
|
||||
// Fetches a key-value secret (kv-v2) after authenticating to Vault via AWS IAM,
|
||||
|
|
|
|||
|
|
@ -42,7 +42,7 @@ The next sections review how the authN/Z workflows work. If you
|
|||
have already reviewed these sections, here are some quick links to:
|
||||
|
||||
- [Usage](/docs/secrets/azure#usage)
|
||||
- [API documentation](/api/auth/azure) docs.
|
||||
- [API documentation](/api-docs/auth/azure) docs.
|
||||
|
||||
## Authentication
|
||||
|
||||
|
|
@ -139,7 +139,7 @@ tool.
|
|||
authentication type, as well as overall constraints and configuration for
|
||||
the generated auth tokens.
|
||||
|
||||
For the complete list of role options, please see the [API documentation](/api/auth/azure).
|
||||
For the complete list of role options, please see the [API documentation](/api-docs/auth/azure).
|
||||
|
||||
### Via the API
|
||||
|
||||
|
|
@ -211,7 +211,7 @@ AZURE_GO_SDK_LOG_LEVEL=DEBUG
|
|||
|
||||
## API
|
||||
|
||||
The Azure Auth Plugin has a full HTTP API. Please see the [API documentation](/api/auth/azure) for more details.
|
||||
The Azure Auth Plugin has a full HTTP API. Please see the [API documentation](/api-docs/auth/azure) for more details.
|
||||
|
||||
## Code Example
|
||||
|
||||
|
|
@ -230,7 +230,7 @@ import (
|
|||
"fmt"
|
||||
|
||||
vault "github.com/hashicorp/vault/api"
|
||||
auth "github.com/hashicorp/vault/api/auth/azure"
|
||||
auth "github.com/hashicorp/vault/api-docs/auth/azure"
|
||||
)
|
||||
|
||||
// Fetches a key-value secret (kv-v2) after authenticating to Vault via Azure authentication.
|
||||
|
|
|
|||
|
|
@ -135,4 +135,4 @@ management tool.
|
|||
## API
|
||||
|
||||
The TLS Certificate auth method has a full HTTP API. Please see the
|
||||
[TLS Certificate API](/api/auth/cert) for more details.
|
||||
[TLS Certificate API](/api-docs/auth/cert) for more details.
|
||||
|
|
|
|||
|
|
@ -295,5 +295,5 @@ match the certificates you're checking.
|
|||
|
||||
## API
|
||||
|
||||
The CF auth method has a full HTTP API. Please see the [CF Auth API](/api/auth/cf)
|
||||
The CF auth method has a full HTTP API. Please see the [CF Auth API](/api-docs/auth/cf)
|
||||
for more details.
|
||||
|
|
|
|||
|
|
@ -359,8 +359,8 @@ The GCP Auth Plugin has a full HTTP API. Please see the
|
|||
[signjwt-method]: https://cloud.google.com/iam/docs/reference/credentials/rest/v1/projects.serviceAccounts/signJwt
|
||||
[cloud-creds]: https://cloud.google.com/docs/authentication/production#providing_credentials_to_your_application
|
||||
[service-accounts]: https://cloud.google.com/compute/docs/access/service-accounts
|
||||
[api-docs]: /api/auth/gcp
|
||||
[identity-group-aliases]: /api/secret/identity/group-alias
|
||||
[api-docs]: /api-docs/auth/gcp
|
||||
[identity-group-aliases]: /api-docs/secret/identity/group-alias
|
||||
[instance-identity]: https://cloud.google.com/compute/docs/instances/verifying-instance-identity
|
||||
[repo]: https://github.com/hashicorp/vault-plugin-auth-gcp
|
||||
|
||||
|
|
|
|||
|
|
@ -109,5 +109,5 @@ management tool.
|
|||
## API
|
||||
|
||||
The GitHub auth method has a full HTTP API. Please see the
|
||||
[GitHub Auth API](/api/auth/github) for more
|
||||
[GitHub Auth API](/api-docs/auth/github) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -154,7 +154,7 @@ EOF
|
|||
|
||||
`cat jwt.json | jq -r .access_token | cut -d. -f2 | base64 -D`
|
||||
|
||||
- As of Vault 1.2, the [`verbose_oidc_logging`](/api/auth/jwt#verbose_oidc_logging) role
|
||||
- As of Vault 1.2, the [`verbose_oidc_logging`](/api-docs/auth/jwt#verbose_oidc_logging) role
|
||||
option is available which will log the received OIDC token to the _server_ logs if debug-level logging is enabled. This can
|
||||
be helpful when debugging provider setup and verifying that the received claims are what you expect.
|
||||
Since claims data is logged verbatim and may contain sensitive information, this option should not be
|
||||
|
|
@ -240,7 +240,7 @@ management tool.
|
|||
|
||||
1. Use the `/config` endpoint to configure Vault. To support JWT roles, either local keys, a JWKS URL, or an OIDC
|
||||
Discovery URL must be present. For OIDC roles, OIDC Discovery URL, OIDC Client ID and OIDC Client Secret are required. For the
|
||||
list of available configuration options, please see the [API documentation](/api/auth/jwt).
|
||||
list of available configuration options, please see the [API documentation](/api-docs/auth/jwt).
|
||||
|
||||
```text
|
||||
$ vault write auth/jwt/config \
|
||||
|
|
@ -345,4 +345,4 @@ JSON Pointer can be used as a selector. Refer to the
|
|||
## API
|
||||
|
||||
The JWT Auth Plugin has a full HTTP API. Please see the
|
||||
[API docs](/api/auth/jwt) for more details.
|
||||
[API docs](/api-docs/auth/jwt) for more details.
|
||||
|
|
|
|||
|
|
@ -70,7 +70,7 @@ You should set up a [Vault policy](https://learn.hashicorp.com/tutorials/vault/p
|
|||
oidc_discovery_url="https://login.microsoftonline.com/tenant_id/v2.0"
|
||||
```
|
||||
|
||||
1. Configure the [OIDC Role](/api/auth/jwt#create-role) with the following:
|
||||
1. Configure the [OIDC Role](/api-docs/auth/jwt#create-role) with the following:
|
||||
- `user_claim` should be `"email"`.
|
||||
- `allowed_redirect_uris` should be the two redirect URIs for Vault CLI and UI access.
|
||||
- `groups_claim` should be set to `"groups"`.
|
||||
|
|
@ -84,16 +84,16 @@ You should set up a [Vault policy](https://learn.hashicorp.com/tutorials/vault/p
|
|||
policies=default
|
||||
```
|
||||
|
||||
1. In Vault, create the [external group](/api/secret/identity/group).
|
||||
1. In Vault, create the [external group](/api-docs/secret/identity/group).
|
||||
Record the group ID as you will need it for the group alias.
|
||||
|
||||
1. From Vault, retrieve the [OIDC accessor ID](/api/system/auth#list-auth-methods)
|
||||
1. From Vault, retrieve the [OIDC accessor ID](/api-docs/system/auth#list-auth-methods)
|
||||
from the OIDC auth method as you will need it for the group alias's `mount_accessor`.
|
||||
|
||||
1. Go to the Azure AD Group you want to attach to Vault's external group. Record the `objectId`
|
||||
as you will need it as the group alias name in Vault.
|
||||
|
||||
1. In Vault, create a [group alias](/api/secret/identity/group-alias)
|
||||
1. In Vault, create a [group alias](/api-docs/secret/identity/group-alias)
|
||||
for the external group and set the `objectId` as the group alias name.
|
||||
```shell
|
||||
vault write identity/group-alias \
|
||||
|
|
@ -168,7 +168,7 @@ Google-specific configuration is available when using Google as an identity prov
|
|||
Vault JWT/OIDC auth method. The configuration allows Vault to obtain Google Workspace group membership and
|
||||
user information during the JWT/OIDC authentication flow. The group membership obtained from Google Workspace
|
||||
may be used for Identity group alias association. The user information obtained from Google Workspace can be
|
||||
used to copy claims data into resulting auth token and alias metadata via [claim_mappings](/api/auth/jwt#claim_mappings).
|
||||
used to copy claims data into resulting auth token and alias metadata via [claim_mappings](/api-docs/auth/jwt#claim_mappings).
|
||||
|
||||
#### Setup
|
||||
|
||||
|
|
@ -209,7 +209,7 @@ host that Vault is running on.
|
|||
- `fetch_user_info` `(bool: false)` - If set to true, user info will be fetched from Google Workspace using the configured [user_custom_schemas](#user_custom_schemas).
|
||||
- `groups_recurse_max_depth` `(int: <optional>)` - Group membership recursion max depth. Defaults to 0, which means don't recurse.
|
||||
- `user_custom_schemas` `(string: <optional>)` - Comma-separated list of Google Workspace [custom schemas](https://developers.google.com/admin-sdk/directory/v1/guides/manage-schemas).
|
||||
Values set for Google Workspace users using custom schema fields will be fetched and made available as claims that can be used with [claim_mappings](/api/auth/jwt#claim_mappings). Required if [fetch_user_info](#fetch_user_info) is set to true.
|
||||
Values set for Google Workspace users using custom schema fields will be fetched and made available as claims that can be used with [claim_mappings](/api-docs/auth/jwt#claim_mappings). Required if [fetch_user_info](#fetch_user_info) is set to true.
|
||||
|
||||
Example configuration:
|
||||
|
||||
|
|
|
|||
|
|
@ -225,5 +225,5 @@ client.
|
|||
## API
|
||||
|
||||
The Kerberos auth method has a full HTTP API. Please see the
|
||||
[Kerberos auth method API](/api/auth/kerberos) for more
|
||||
[Kerberos auth method API](/api-docs/auth/kerberos) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -81,7 +81,7 @@ management tool.
|
|||
1. Use the `/config` endpoint to configure Vault to talk to Kubernetes. Use
|
||||
`kubectl cluster-info` to validate the Kubernetes host address and TCP port.
|
||||
For the list of available configuration options, please see the
|
||||
[API documentation](/api/auth/kubernetes).
|
||||
[API documentation](/api-docs/auth/kubernetes).
|
||||
|
||||
```bash
|
||||
vault write auth/kubernetes/config \
|
||||
|
|
@ -112,7 +112,7 @@ management tool.
|
|||
namespace and it gives it the default policy.
|
||||
|
||||
For the complete list of configuration options, please see the [API
|
||||
documentation](/api/auth/kubernetes).
|
||||
documentation](/api-docs/auth/kubernetes).
|
||||
|
||||
## Kubernetes 1.21
|
||||
|
||||
|
|
@ -326,7 +326,7 @@ subjects:
|
|||
## API
|
||||
|
||||
The Kubernetes Auth Plugin has a full HTTP API. Please see the
|
||||
[API docs](/api/auth/kubernetes) for more details.
|
||||
[API docs](/api-docs/auth/kubernetes) for more details.
|
||||
|
||||
[k8s-tokenreview]: https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.22/#tokenreview-v1-authentication-k8s-io
|
||||
|
||||
|
|
@ -347,7 +347,7 @@ import (
|
|||
"os"
|
||||
|
||||
vault "github.com/hashicorp/vault/api"
|
||||
auth "github.com/hashicorp/vault/api/auth/kubernetes"
|
||||
auth "github.com/hashicorp/vault/api-docs/auth/kubernetes"
|
||||
)
|
||||
|
||||
// Fetches a key-value secret (kv-v2) after authenticating to Vault with a Kubernetes service account.
|
||||
|
|
|
|||
|
|
@ -267,5 +267,5 @@ It should be noted that user -> policy mapping happens at token creation time. A
|
|||
## API
|
||||
|
||||
The LDAP auth method has a full HTTP API. Please see the
|
||||
[LDAP auth method API](/api/auth/ldap) for more
|
||||
[LDAP auth method API](/api-docs/auth/ldap) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -80,7 +80,7 @@ The Step-up Enterprise MFA uses the combination of mount accessors plus a `usern
|
|||
| ---------------------------------------------- | ----------------------------------------------------------------------------------------- | ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- |
|
||||
| [Login MFA](/docs/auth/login-mfa) | CLI/API. The UI does not support the configuration of Login MFA as of Vault version 1.10. | Configured using the `identity/mfa/method` endpoints, then passing those method IDs to the `identity/mfa/login-enforcement` endpoint. MFA methods supported: TOTP, Okta, Duo, PingID. |
|
||||
| [Okta Auth MFA](/docs/auth/okta) | CLI/API | MFA methods supported: [TOTP](https://help.okta.com/en/prod/Content/Topics/Security/mfa-totp-seed.htm) , [Okta Verify Push](https://help.okta.com/en/prod/Content/Topics/Mobile/ov-admin-config.htm). Note that Vault does not support Okta Verify Push with Number Challenge at this time. |
|
||||
| [Step-up Enterprise MFA](/docs/enterprise/mfa) | CLI/API | [Configured](/api/system/mfa) using the `sys/mfa/method` endpoints and by referencing those methods in policies. MFA Methods supported: TOTP, Okta, Duo, PingID |
|
||||
| [Step-up Enterprise MFA](/docs/enterprise/mfa) | CLI/API | [Configured](/api-docs/system/mfa) using the `sys/mfa/method` endpoints and by referencing those methods in policies. MFA Methods supported: TOTP, Okta, Duo, PingID |
|
||||
|
||||
### Q: Which MFA mechanism is used with the different MFA workflows in Vault version 1.10?
|
||||
|
||||
|
|
|
|||
|
|
@ -40,9 +40,9 @@ MFA in Vault includes the following login types:
|
|||
## Login MFA Procedure
|
||||
|
||||
Login MFA can be configured to secure further authenticating to an auth method. To enable login
|
||||
MFA, an MFA method needs to be configured. Please see [Login MFA API](/api/secret/identity/mfa) for details
|
||||
MFA, an MFA method needs to be configured. Please see [Login MFA API](/api-docs/secret/identity/mfa) for details
|
||||
on how to configure an MFA method. Once an MFA method is configured, an operator can configure an MFA enforcement using the returned unique MFA method ID.
|
||||
Please see [Login MFA Enforcement API](/api/secret/identity/mfa/login-enforcement)
|
||||
Please see [Login MFA Enforcement API](/api-docs/secret/identity/mfa/login-enforcement)
|
||||
for details on how to configure an MFA enforcement config. MFA could be enforced for an entity, a group of
|
||||
entities, a specific auth method accessor, or an auth method type. A login request that matches
|
||||
any MFA enforcement restrictions is subject to further MFA validation,
|
||||
|
|
@ -131,10 +131,10 @@ note that this can affect the login response on any auth mount protected by MFA
|
|||
|
||||
Note that the `uses_passcode` boolean value is always set to true for TOTP, and must always be set to false for Okta and PingID.
|
||||
For Duo method, the value can be configured as part of the method configuration.
|
||||
Please see [Duo API](/api/secret/identity/mfa/duo) for details
|
||||
Please see [Duo API](/api-docs/secret/identity/mfa/duo) for details
|
||||
on how to configure the boolean value for Duo.
|
||||
|
||||
To validate the MFA restricted login request, the user sends a second request to the [validate](/api/system/mfa/validate)
|
||||
To validate the MFA restricted login request, the user sends a second request to the [validate](/api-docs/system/mfa/validate)
|
||||
endpoint including the MFA request ID and MFA payload. MFA payload contains a map of methodIDs and their associated credentials.
|
||||
If the configured MFA methods, such as PingID, Okta, and Duo, do not require a passcode, the associated
|
||||
credentials will be a list with one empty string.
|
||||
|
|
|
|||
|
|
@ -199,4 +199,4 @@ POST http://127.0.0.1/v1/auth/oci/login/devrole
|
|||
|
||||
## API
|
||||
|
||||
The OCI Auth method has a full HTTP API. Please see the [API docs](/api/auth/oci) for more details.
|
||||
The OCI Auth method has a full HTTP API. Please see the [API docs](/api-docs/auth/oci) for more details.
|
||||
|
|
|
|||
|
|
@ -130,4 +130,4 @@ management tool.
|
|||
## API
|
||||
|
||||
The Okta auth method has a full HTTP API. Please see the
|
||||
[Okta Auth API](/api/auth/okta) for more details.
|
||||
[Okta Auth API](/api-docs/auth/okta) for more details.
|
||||
|
|
|
|||
|
|
@ -78,5 +78,5 @@ The response will contain a token at `auth.client_token`:
|
|||
## API
|
||||
|
||||
The RADIUS auth method has a full HTTP API. Please see the
|
||||
[RADIUS Auth API](/api/auth/radius) for more
|
||||
[RADIUS Auth API](/api-docs/auth/radius) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -36,5 +36,5 @@ either `X-Vault-Token: <token>` or `Authorization: Bearer <token>`.
|
|||
## API
|
||||
|
||||
The Token auth method has a full HTTP API. Please see the
|
||||
[Token auth method API](/api/auth/token) for more
|
||||
[Token auth method API](/api-docs/auth/token) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -84,4 +84,4 @@ management tool.
|
|||
## API
|
||||
|
||||
The Userpass auth method has a full HTTP API. Please see the [Userpass auth
|
||||
method API](/api/auth/userpass) for more details.
|
||||
method API](/api-docs/auth/userpass) for more details.
|
||||
|
|
|
|||
|
|
@ -28,7 +28,7 @@ $ vault delete transit/keys/my-key
|
|||
```
|
||||
|
||||
Note: changing the `deletion_allowed` parameter to `true` is necessary for the
|
||||
key to be successfully deleted, you can read more on key parameters [here](/api/secret/transit#update-key-configuration)
|
||||
key to be successfully deleted, you can read more on key parameters [here](/api-docs/secret/transit#update-key-configuration)
|
||||
|
||||
Delete an IAM role:
|
||||
|
||||
|
|
|
|||
|
|
@ -59,7 +59,7 @@ vault <command> [options] [path] [args]
|
|||
The following `write` command creates a new user (`bob`) in the userpass auth
|
||||
method. It passes the `-address` flag to specify the Vault server address which
|
||||
precedes the path (`auth/userpass/users/bob`) and its
|
||||
[argument](/api/auth/userpass#create-update-user)
|
||||
[argument](/api-docs/auth/userpass#create-update-user)
|
||||
(`password="long-password"`) at last.
|
||||
|
||||
```shell-session
|
||||
|
|
@ -67,7 +67,7 @@ $ vault write -address="http://127.0.0.1:8200" auth/userpass/users/bob password=
|
|||
```
|
||||
|
||||
If multiple options (`-address` and `-namespace`) and
|
||||
[arguments](/api/auth/userpass#create-update-user) (`password` and
|
||||
[arguments](/api-docs/auth/userpass#create-update-user) (`password` and
|
||||
`policies`) are specified, the command would look like:
|
||||
|
||||
```shell-session
|
||||
|
|
@ -302,7 +302,7 @@ limiting is off by default.
|
|||
_Note:_ The rate is limited for each invocation of the `vault` CLI. Since
|
||||
each invocation of the `vault` CLI typically only makes a few requests,
|
||||
this environment variable is most useful when using the Go
|
||||
[Vault client API](/api/libraries#go).
|
||||
[Vault client API](/api-docs/libraries#go).
|
||||
|
||||
### `VAULT_NAMESPACE`
|
||||
|
||||
|
|
|
|||
|
|
@ -128,7 +128,7 @@ import (
|
|||
"log"
|
||||
|
||||
vault "github.com/hashicorp/vault/api"
|
||||
auth "github.com/hashicorp/vault/api/auth/userpass"
|
||||
auth "github.com/hashicorp/vault/api-docs/auth/userpass"
|
||||
)
|
||||
|
||||
// Once you've set the token for your Vault client, you will need to
|
||||
|
|
|
|||
|
|
@ -35,7 +35,7 @@ When anything authenticates to Vault, be it a user, application, machine, etc.,
|
|||
|
||||
## But wait, there’s more...
|
||||
|
||||
Want to take full advantage of the Vault identity system and how clients are counted? The Vault identity system also has [Entity Aliases](https://www.vaultproject.io/api/secret/identity/entity-alias) and [Identity Groups](https://www.vaultproject.io/api-docs/secret/identity/group-alias).
|
||||
Want to take full advantage of the Vault identity system and how clients are counted? The Vault identity system also has [Entity Aliases](/api-docs/secret/identity/entity-alias) and [Identity Groups](/api-docs/secret/identity/group-alias).
|
||||
|
||||
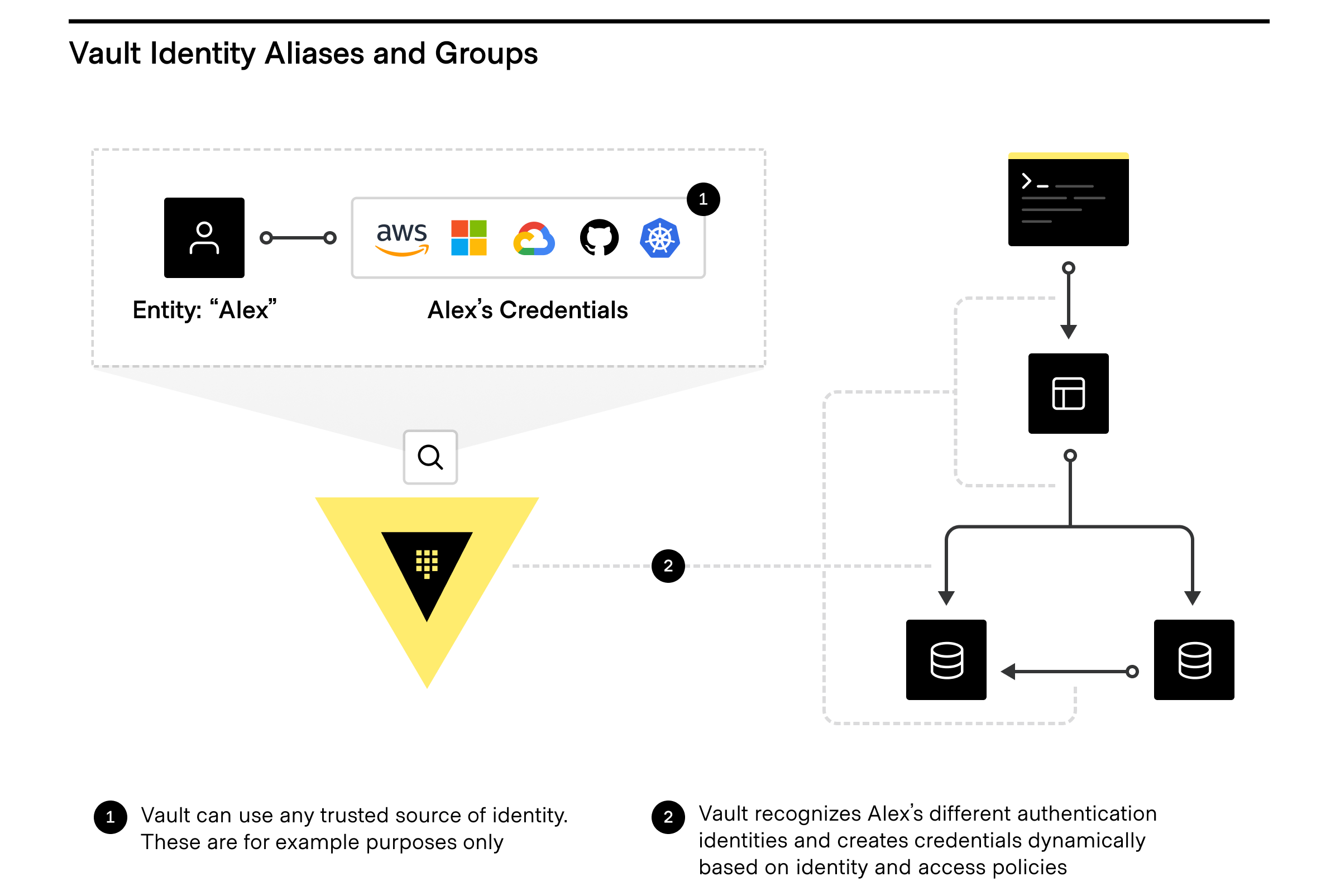
|
||||
|
||||
|
|
@ -90,23 +90,23 @@ How does this relate to Vault clients? As outlined above, and as an example, if
|
|||
| **Auth method** | **Name reported by auth method** |
|
||||
| ------------------------------------------------------------------------------------------------ | ---------------------------------------------------------------------------------- |
|
||||
| **[AliCloud](https://www.vaultproject.io/docs/auth/alicloud)** | Principal ID |
|
||||
| **[AppRole](https://www.vaultproject.io/api-docs/auth/approle#create-update-approle)** | Role ID |
|
||||
| **[AppRole](/api-docs/auth/approle#create-update-approle)** | Role ID |
|
||||
| **[AWS IAM](https://www.vaultproject.io/docs/auth/aws#iam-auth-method)** | Configurable via iam_alias to one of: Role ID (default), IAM unique ID, Full ARN |
|
||||
| **[AWS EC2](https://www.vaultproject.io/docs/auth/aws#ec2-auth-method)** | Configurable via ec2_alias to one of: Role ID (default), EC2 instance ID, AMI ID |
|
||||
| **[Azure](https://www.vaultproject.io/api-docs/auth/azure#create-role)** | Subject (from JWT claim) |
|
||||
| **[Azure](/api-docs/auth/azure#create-role)** | Subject (from JWT claim) |
|
||||
| **[Cloud Foundry](https://www.vaultproject.io/docs/auth/cf)** | App ID |
|
||||
| **[GitHub](https://www.vaultproject.io/docs/auth/github)** | User login name associated with token |
|
||||
| **[Google Cloud](https://www.vaultproject.io/api-docs/auth/gcp#create-role)** | Configurable via iam_alias to one of: Role ID (default), Service account unique ID |
|
||||
| **[JWT/OIDC](https://www.vaultproject.io/api-docs/auth/jwt#create-role)** | Configurable via user_claim to one of the presented claims (no default value) |
|
||||
| **[Google Cloud](/api-docs/auth/gcp#create-role)** | Configurable via iam_alias to one of: Role ID (default), Service account unique ID |
|
||||
| **[JWT/OIDC](/api-docs/auth/jwt#create-role)** | Configurable via user_claim to one of the presented claims (no default value) |
|
||||
| **[Kerberos](https://www.vaultproject.io/docs/auth/kerberos)** | Username |
|
||||
| **[Kubernetes](https://www.vaultproject.io/api-docs/auth/kubernetes#create-role)** | Service account UID |
|
||||
| **[Kubernetes](/api-docs/auth/kubernetes#create-role)** | Service account UID |
|
||||
| **[LDAP](https://www.vaultproject.io/docs/auth/ldap)** | Username |
|
||||
| **[OCI](https://www.vaultproject.io/api-docs/auth/oci#create-role)** | Rolename |
|
||||
| **[Okta](https://www.vaultproject.io/api-docs/auth/okta#register-user)** | Username |
|
||||
| **[OCI](/api-docs/auth/oci#create-role)** | Rolename |
|
||||
| **[Okta](/api-docs/auth/okta#register-user)** | Username |
|
||||
| **[RADIUS](https://www.vaultproject.io/docs/auth/radius)** | Username |
|
||||
| **[TLS Certificate](https://www.vaultproject.io/api-docs/auth/cert#create-ca-certificate-role)** | Subject CommonName |
|
||||
| **[TLS Certificate](/api-docs/auth/cert#create-ca-certificate-role)** | Subject CommonName |
|
||||
| **[Token](https://www.vaultproject.io/docs/auth/token)** | entity_alias, if provided (Note: please ensure that entity_alias is always used) |
|
||||
| **[Username/Password](https://www.vaultproject.io/api-docs/auth/userpass#create-update-user)** | Username |
|
||||
| **[Username/Password](/api-docs/auth/userpass#create-update-user)** | Username |
|
||||
|
||||
## Considerations with CI/CD
|
||||
|
||||
|
|
@ -213,7 +213,7 @@ entity_id n/a
|
|||
|
||||
To reduce the number of non-entity tokens in use, consider switching to an authentication method such as
|
||||
[AppRole](/docs/auth/approle) instead of handing out directly-created tokens. Ensure that entities and
|
||||
[entity aliases](/api/secret/identity/entity-alias) exist for all login methods used to create batch tokens.
|
||||
[entity aliases](/api-docs/secret/identity/entity-alias) exist for all login methods used to create batch tokens.
|
||||
|
||||
### Tracking non-entity tokens
|
||||
|
||||
|
|
@ -242,7 +242,7 @@ request; this can happen if the request is unauthenticated, or made with a root
|
|||
|
||||
## API and Permissions
|
||||
|
||||
Please see [Client Count API](/api/system/internal-counters#client-count) for more details. Note that this API is marked as
|
||||
Please see [Client Count API](/api-docs/system/internal-counters#client-count) for more details. Note that this API is marked as
|
||||
"internal" so its behavior or format may change without warning. The UI is the preferred means of interacting with the
|
||||
client count feature.
|
||||
|
||||
|
|
|
|||
|
|
@ -49,7 +49,7 @@ Raft clusters deployed with older versions of Vault will also transition to use
|
|||
Autopilot automatically.
|
||||
|
||||
Autopilot exposes a [configuration
|
||||
API](/api/system/storage/raftautopilot#set-configuration) to manage its
|
||||
API](/api-docs/system/storage/raftautopilot#set-configuration) to manage its
|
||||
behavior. Autopilot gets initialized with the following default values.
|
||||
|
||||
- `cleanup_dead_servers` - `false`
|
||||
|
|
@ -72,7 +72,7 @@ independently of their primary.
|
|||
|
||||
DR secondary clusters will also have their own Autopilot configuration (starting
|
||||
in Vault 1.8.0), managed independently of their primary. The [Autopilot
|
||||
API](/api/system/storage/raftautopilot) uses DR operation tokens for
|
||||
API](/api-docs/system/storage/raftautopilot) uses DR operation tokens for
|
||||
authorization.
|
||||
|
||||
## Learn
|
||||
|
|
|
|||
|
|
@ -70,4 +70,4 @@ step-by-step tutorial.
|
|||
## API
|
||||
|
||||
Rate limit quotas can be managed over the HTTP API. Please see
|
||||
[Rate Limit Quotas API](/api/system/rate-limit-quotas) for more details.
|
||||
[Rate Limit Quotas API](/api-docs/system/rate-limit-quotas) for more details.
|
||||
|
|
|
|||
|
|
@ -70,7 +70,7 @@ used for just enough initial setup (usually, setting up auth methods
|
|||
and policies necessary to allow administrators to acquire more limited tokens)
|
||||
or in emergencies, and are revoked immediately after they are no longer needed.
|
||||
If a new root token is needed, the `operator generate-root` command and associated
|
||||
[API endpoint](/api/system/generate-root) can be used to generate one on-the-fly.
|
||||
[API endpoint](/api-docs/system/generate-root) can be used to generate one on-the-fly.
|
||||
|
||||
It is also good security practice for there to be multiple eyes on a terminal
|
||||
whenever a root token is live. This way multiple people can verify as to the
|
||||
|
|
@ -159,7 +159,7 @@ token's information is looked up. It is based on a combination of factors:
|
|||
1. The system max TTL, which is 32 days but can be changed in Vault's
|
||||
configuration file.
|
||||
2. The max TTL set on a mount using [mount
|
||||
tuning](/api/system/mounts). This value
|
||||
tuning](/api-docs/system/mounts). This value
|
||||
is allowed to override the system max TTL -- it can be longer or shorter,
|
||||
and if set this value will be respected.
|
||||
3. A value suggested by the auth method that issued the token. This
|
||||
|
|
|
|||
|
|
@ -26,9 +26,9 @@ advertise the correct address to other nodes.
|
|||
As of version 1.9, Vault supports defining custom HTTP response headers for the root path (`/`) and also on API endpoints (`/v1/*`).
|
||||
The headers are defined based on the returned status code. For example, a user can define a list of
|
||||
custom response headers for the `200` status code, and another list of custom response headers for
|
||||
the `307` status code. There is a `"/sys/config/ui"` [API endpoint](/api/system/config-ui) which allows users
|
||||
the `307` status code. There is a `"/sys/config/ui"` [API endpoint](/api-docs/system/config-ui) which allows users
|
||||
to set `UI` specific custom headers. If a header is configured in a configuration file, it is not allowed
|
||||
to be reconfigured through the `"/sys/config/ui"` [API endpoint](/api/system/config-ui). In cases where a
|
||||
to be reconfigured through the `"/sys/config/ui"` [API endpoint](/api-docs/system/config-ui). In cases where a
|
||||
custom header value needs to be modified or the custom header needs to be removed, the Vault's configuration file
|
||||
needs to be modified accordingly, and a `SIGHUP` signal needs to be sent to the Vault process.
|
||||
|
||||
|
|
@ -40,11 +40,11 @@ upon start up indicating the header with `X-Vault-` prefix is not accepted.
|
|||
### Order of precedence
|
||||
|
||||
If the same header is configured in both the configuration file and
|
||||
in the `"/sys/config/ui"` [API endpoint](/api/system/config-ui), the header in the configuration file takes precedence.
|
||||
in the `"/sys/config/ui"` [API endpoint](/api-docs/system/config-ui), the header in the configuration file takes precedence.
|
||||
For example, the `"Content-Security-Policy"` header is defined by default in the
|
||||
`"/sys/config/ui"` [API endpoint](/api/system/config-ui). If that header is also defined in the configuration file,
|
||||
`"/sys/config/ui"` [API endpoint](/api-docs/system/config-ui). If that header is also defined in the configuration file,
|
||||
the value in the configuration file is set in the response headers instead of the
|
||||
default value in the `"/sys/config/ui"` [API endpoint](/api/system/config-ui).
|
||||
default value in the `"/sys/config/ui"` [API endpoint](/api-docs/system/config-ui).
|
||||
|
||||
## `tcp` Listener Parameters
|
||||
|
||||
|
|
|
|||
|
|
@ -112,7 +112,7 @@ path "<mount path>/decrypt/<key name>" {
|
|||
## Key Rotation
|
||||
|
||||
This seal supports key rotation using the Transit Secret Engine's key rotation endpoints. See
|
||||
[doc](/api/secret/transit#rotate-key). Old keys must not be disabled or deleted and are
|
||||
[doc](/api-docs/secret/transit#rotate-key). Old keys must not be disabled or deleted and are
|
||||
used to decrypt older data.
|
||||
|
||||
## Learn
|
||||
|
|
|
|||
|
|
@ -211,4 +211,4 @@ guide for a step-by-step tutorial.
|
|||
## API
|
||||
|
||||
Control Groups can be managed over the HTTP API. Please see
|
||||
[Control Groups API](/api/system/control-group) for more details.
|
||||
[Control Groups API](/api-docs/system/control-group) for more details.
|
||||
|
|
|
|||
|
|
@ -15,7 +15,7 @@ effect when using Vault with an HSM.
|
|||
|
||||
Normally, Vault uses a single set of unseal keys to perform both decryption of
|
||||
the cryptographic barrier and to authorize recovery operations, such as the
|
||||
[`generate-root`](/api/system/generate-root)
|
||||
[`generate-root`](/api-docs/system/generate-root)
|
||||
functionality.
|
||||
|
||||
When using an HSM, because the HSM automatically unseals the barrier but
|
||||
|
|
@ -55,7 +55,7 @@ keys for this purpose, rather than the barrier unseal keys, is automatic.
|
|||
|
||||
When initializing, the split is performed according to the following CLI flags
|
||||
and their API equivalents in the
|
||||
[/sys/init](/api/system/init) endpoint:
|
||||
[/sys/init](/api-docs/system/init) endpoint:
|
||||
|
||||
- `recovery-shares`: The number of shares into which to split the recovery
|
||||
key. This value is equivalent to the `recovery_shares` value in the API
|
||||
|
|
@ -90,7 +90,7 @@ this is performed by using the `-target=recovery` flag to `vault operator rekey`
|
|||
|
||||
Via the API, the rekey operation is performed with the same parameters as the
|
||||
[normal `/sys/rekey`
|
||||
endpoint](/api/system/rekey); however, the
|
||||
endpoint](/api-docs/system/rekey); however, the
|
||||
API prefix for this operation is at `/sys/rekey-recovery-key` rather than
|
||||
`/sys/rekey`.
|
||||
|
||||
|
|
|
|||
|
|
@ -52,4 +52,4 @@ step-by-step tutorial.
|
|||
## API
|
||||
|
||||
Lease count quotas can be managed over the HTTP API. Please see
|
||||
[Lease Count Quotas API](/api/system/lease-count-quotas) for more details.
|
||||
[Lease Count Quotas API](/api-docs/system/lease-count-quotas) for more details.
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@ description: An overview of license autoloading.
|
|||
|
||||
Prior to Vault 1.8, Vault Enterprise would be licensed using special binaries
|
||||
that contained embedded licenses, or via a license written into Vault storage
|
||||
using the [POST sys/license API](/api/system/license#install-license).
|
||||
using the [POST sys/license API](/api-docs/system/license#install-license).
|
||||
|
||||
As of Vault 1.8 those options still exist but are deprecated, and the recommended
|
||||
mechanism for managing licenses is called License Autoloading. New clusters are
|
||||
|
|
@ -30,4 +30,4 @@ are discrepancies.
|
|||
If autoloading is used, any existing stored license will be ignored. The presence
|
||||
of a stored license in conjunction with an autoloaded license will also result in
|
||||
logged warnings. Once a migration to autoloading is completed, it is recommended to use
|
||||
the [DELETE API](/api/system/license#delete-license) to remove the stored license.
|
||||
the [DELETE API](/api-docs/system/license#delete-license) to remove the stored license.
|
||||
|
|
|
|||
|
|
@ -29,7 +29,7 @@ Support for additional integrations may be added in the future.
|
|||
|
||||
## Plugin Support
|
||||
|
||||
The [PKI Secrets Engine](/api/secret/pki#managed-keys) has been integrated
|
||||
The [PKI Secrets Engine](/api-docs/secret/pki#managed-keys) has been integrated
|
||||
with Managed Keys to offer certificate generation, both root and intermediary
|
||||
PKI paths, leveraging private keys from an external trusted KMS.
|
||||
|
||||
|
|
@ -39,4 +39,4 @@ Managed Keys can be managed over the HTTP API. Please see
|
|||
[Managed Keys API](/api-docs/system/managed-keys) for more details.
|
||||
|
||||
To configure PKI secrets engine with Managed Keys please see
|
||||
[PKI Secret API](/api/secret/pki#managed-keys)
|
||||
[PKI Secret API](/api-docs/secret/pki#managed-keys)
|
||||
|
|
|
|||
|
|
@ -41,7 +41,7 @@ MFA in Vault can be of the following types.
|
|||
## Configuring MFA Methods
|
||||
|
||||
MFA methods are globally managed within the `System Backend` using the HTTP API.
|
||||
Please see [MFA API](/api/system/mfa) for details on how to configure an MFA
|
||||
Please see [MFA API](/api-docs/system/mfa) for details on how to configure an MFA
|
||||
method.
|
||||
|
||||
## MFA Methods In Policies
|
||||
|
|
@ -112,4 +112,4 @@ $ curl \
|
|||
|
||||
### API
|
||||
|
||||
MFA can be managed entirely over the HTTP API. Please see [MFA API](/api/system/mfa) for more details.
|
||||
MFA can be managed entirely over the HTTP API. Please see [MFA API](/api-docs/system/mfa) for more details.
|
||||
|
|
|
|||
|
|
@ -53,7 +53,7 @@ based on consul configuration).
|
|||
|
||||
Additionally, if you wish to point your load balancers at performance standby
|
||||
nodes, the `sys/health` endpoint can be used to determine if a node is a
|
||||
performance standby. See the [sys/health API](/api/system/health) docs for
|
||||
performance standby. See the [sys/health API](/api-docs/system/health) docs for
|
||||
more info.
|
||||
|
||||
## Disabling Performance Standbys
|
||||
|
|
|
|||
|
|
@ -123,7 +123,7 @@ DR is designed to be a mechanism to protect against catastrophic failure of enti
|
|||
They do not forward service read or write requests until they are elected and become a new primary.
|
||||
|
||||
|
||||
For more information on the capabilities of performance and disaster recovery replication, see the Vault Replication [API Documentation](/api/system/replication).
|
||||
For more information on the capabilities of performance and disaster recovery replication, see the Vault Replication [API Documentation](/api-docs/system/replication).
|
||||
|
||||
## Primary and Secondary Cluster Compatibility
|
||||
|
||||
|
|
@ -230,5 +230,5 @@ Refer to the following tutorials replication setup and best practices:
|
|||
## API
|
||||
|
||||
The Vault replication component has a full HTTP API. Please see the
|
||||
[Vault Replication API](/api/system/replication) for more
|
||||
[Vault Replication API](/api-docs/system/replication) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -89,7 +89,7 @@ able to glean from the original request alone.
|
|||
|
||||
Sentinel policies can be configured via the `sys/policies/rgp/` and
|
||||
`sys/policies/egp/` endpoints; see [the
|
||||
documentation](/api/system/policies) for more information.
|
||||
documentation](/api-docs/system/policies) for more information.
|
||||
|
||||
Once set, RGPs can be assigned to Identity entities and groups or to tokens
|
||||
just like ACL policies. As a result, they cannot share names with ACL policies.
|
||||
|
|
|
|||
|
|
@ -113,7 +113,7 @@ make sure the executable referenced in the command exists in the plugin
|
|||
directory. When added to the catalog the plugin is not automatically executed,
|
||||
it instead becomes visible to backends and can be executed by them. For more
|
||||
information on the plugin catalog please see the [Plugin Catalog API
|
||||
docs](/api/system/plugins-catalog).
|
||||
docs](/api-docs/system/plugins-catalog).
|
||||
|
||||
An example of plugin registration in current versions of Vault:
|
||||
|
||||
|
|
|
|||
|
|
@ -10,7 +10,7 @@ description: >-
|
|||
|
||||
## Launching the Vault AMI
|
||||
|
||||
When Vault is first launched from an official Marketplace AMI, it will come up in an uninitialized state and must be initialized via the [API](/api/system/init), [CLI](/docs/commands/operator/init), or UI. The Marketplace AMI listens on port 8200 by default. It is recommended to restrict ingress networking to the Vault instance as much as possible when initially deploying Vault (through EC2 security groups or otherwise) because anyone with network access to Vault will be able to initialize it. To learn more about the default listener configuration, or to make changes, please see the [Vault Deployment Guide](https://learn.hashicorp.com/vault/operations/ops-deployment-guide#listener-stanza).
|
||||
When Vault is first launched from an official Marketplace AMI, it will come up in an uninitialized state and must be initialized via the [API](/api-docs/system/init), [CLI](/docs/commands/operator/init), or UI. The Marketplace AMI listens on port 8200 by default. It is recommended to restrict ingress networking to the Vault instance as much as possible when initially deploying Vault (through EC2 security groups or otherwise) because anyone with network access to Vault will be able to initialize it. To learn more about the default listener configuration, or to make changes, please see the [Vault Deployment Guide](https://learn.hashicorp.com/vault/operations/ops-deployment-guide#listener-stanza).
|
||||
|
||||
Additionally on first launch, a new self-signed [certificate](/docs/configuration/listener/tcp#tls_cert_file) and [key](/docs/configuration/listener/tcp#tls_key_file) (unique to the EC2 instance) will be generated to secure Vault traffic using TLS. This is provided as a “more secure” (vs. unencrypted TCP traffic) temporary solution, but it is strongly recommended to replace these with your own certificate and key. Please note that when using a self-signed certificate, Vault clients will need to [skip](/docs/commands#vault_skip_verify) the verification of Vault’s certificate, which voids Vault’s [security model](/docs/internals/security).
|
||||
|
||||
|
|
|
|||
|
|
@ -76,7 +76,7 @@ The following parameters are supported by the Vault provider:
|
|||
|
||||
- `secretPath` `(string: "")` - The path in Vault where the secret is located.
|
||||
For secrets that are retrieved via HTTP GET method, the `secretPath` can include optional URI parameters,
|
||||
for example, the [version of the KV2 secret](https://www.vaultproject.io/api/secret/kv/kv-v2#read-secret-version):
|
||||
for example, the [version of the KV2 secret](https://www.vaultproject.io/api-docs/secret/kv/kv-v2#read-secret-version):
|
||||
|
||||
```yaml
|
||||
objects: |
|
||||
|
|
@ -97,5 +97,5 @@ The following parameters are supported by the Vault provider:
|
|||
```
|
||||
|
||||
~> `secretArgs` are sent as part of the HTTP request body. Therefore, they are only effective for HTTP PUT/POST requests, for instance,
|
||||
the [request used to generate a new certificate](https://www.vaultproject.io/api/secret/pki#generate-certificate).
|
||||
the [request used to generate a new certificate](https://www.vaultproject.io/api-docs/secret/pki#generate-certificate).
|
||||
To supply additional parameters for secrets retrieved via HTTP GET, include optional URI paramters in [`secretPath`](#secretpath).
|
||||
|
|
@ -15,7 +15,7 @@ This is designed for a high-load environment where many instances may be accessi
|
|||
a shared password simultaneously. With a simple set up and a simple creds API,
|
||||
it doesn't require instances to be manually registered in advance to gain access.
|
||||
As long as access has been granted to the creds path via a method like
|
||||
[AppRole](/api/auth/approle), they're available. Passwords are
|
||||
[AppRole](/api-docs/auth/approle), they're available. Passwords are
|
||||
lazily rotated based on preset TTLs and can have a length configured to meet your needs. Additionally,
|
||||
passwords can be manually rotated using the [rotate-role](/api-docs/secret/ad#rotate-role-credentials) endpoint.
|
||||
|
||||
|
|
@ -123,7 +123,7 @@ management tool.
|
|||
```
|
||||
|
||||
4. Grant "my-application" access to its creds at `ad/creds/my-application` using an
|
||||
auth method like [AppRole](/api/auth/approle).
|
||||
auth method like [AppRole](/api-docs/auth/approle).
|
||||
|
||||
### FAQ
|
||||
|
||||
|
|
@ -355,5 +355,5 @@ for a step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The Active Directory secrets engine has a full HTTP API. Please see the
|
||||
[Active Directory secrets engine API](/api/secret/ad) for more
|
||||
[Active Directory secrets engine API](/api-docs/secret/ad) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -207,5 +207,5 @@ the proper permission, it can generate credentials.
|
|||
## API
|
||||
|
||||
The AliCloud secrets engine has a full HTTP API. Please see the
|
||||
[AliCloud secrets engine API](/api/secret/alicloud) for more
|
||||
[AliCloud secrets engine API](/api-docs/secret/alicloud) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -164,7 +164,7 @@ the proper permission, it can generate credentials.
|
|||
~> **Note:** Due to AWS eventual consistency, after calling the
|
||||
`aws/config/rotate-root` endpoint, subsequent calls from Vault to
|
||||
AWS may fail for a few seconds until AWS becomes consistent again.
|
||||
See the [AWS secrets engine API](/api/secret/aws#rotate-root-iam-credentials)
|
||||
See the [AWS secrets engine API](/api-docs/secret/aws#rotate-root-iam-credentials)
|
||||
for further information on `config/rotate-root` functionality.
|
||||
|
||||
## Example IAM Policy for Vault
|
||||
|
|
@ -479,5 +479,5 @@ errors for exceeding the AWS limit of 32 characters on STS token names.
|
|||
## API
|
||||
|
||||
The AWS secrets engine has a full HTTP API. Please see the
|
||||
[AWS secrets engine API](/api/secret/aws) for more
|
||||
[AWS secrets engine API](/api-docs/secret/aws) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -352,6 +352,6 @@ for a step-by-step tutorial.
|
|||
The Azure secrets engine has a full HTTP API. Please see the [Azure secrets engine API docs][api]
|
||||
for more details.
|
||||
|
||||
[api]: /api/secret/azure
|
||||
[config]: /api/secret/azure#configure-access
|
||||
[api]: /api-docs/secret/azure
|
||||
[config]: /api-docs/secret/azure#configure-access
|
||||
[repo]: https://github.com/hashicorp/vault-plugin-secrets-azure
|
||||
|
|
|
|||
|
|
@ -160,7 +160,7 @@ step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The Consul secrets engine has a full HTTP API. Please see the
|
||||
[Consul secrets engine API](/api/secret/consul) for more
|
||||
[Consul secrets engine API](/api-docs/secret/consul) for more
|
||||
details.
|
||||
|
||||
[consul-mgmt-token]: https://www.consul.io/docs/agent/http/acl.html#acl_create
|
||||
|
|
|
|||
|
|
@ -59,5 +59,5 @@ guide for a step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The Cubbyhole secrets engine has a full HTTP API. Please see the
|
||||
[Cubbyhole secrets engine API](/api/secret/cubbyhole) for more
|
||||
[Cubbyhole secrets engine API](/api-docs/secret/cubbyhole) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -88,6 +88,6 @@ the proper permission, it can generate credentials.
|
|||
|
||||
## API
|
||||
|
||||
The full list of configurable options can be seen in the [Cassandra database plugin API](/api/secret/databases/cassandra) page.
|
||||
The full list of configurable options can be seen in the [Cassandra database plugin API](/api-docs/secret/databases/cassandra) page.
|
||||
|
||||
For more information on the database secrets engine's HTTP API please see the [Database secret secrets engine API](/api/secret/databases) page.
|
||||
For more information on the database secrets engine's HTTP API please see the [Database secret secrets engine API](/api-docs/secret/databases) page.
|
||||
|
|
|
|||
|
|
@ -175,7 +175,7 @@ the proper permission, it can generate credentials.
|
|||
|
||||
## API
|
||||
|
||||
The full list of configurable options can be seen in the [Elasticsearch database plugin API](/api/secret/databases/elasticdb.html) page.
|
||||
The full list of configurable options can be seen in the [Elasticsearch database plugin API](/api-docs/secret/databases/elasticdb.html) page.
|
||||
|
||||
For more information on the database secrets engine's HTTP API please see the
|
||||
[Database secrets engine API](/api/secret/databases) page.
|
||||
[Database secrets engine API](/api-docs/secret/databases) page.
|
||||
|
|
|
|||
|
|
@ -79,7 +79,7 @@ the proper permission, it can generate credentials.
|
|||
|
||||
## API
|
||||
|
||||
The full list of configurable options can be seen in the [HANA database plugin API](/api/secret/databases/hanadb) page.
|
||||
The full list of configurable options can be seen in the [HANA database plugin API](/api-docs/secret/databases/hanadb) page.
|
||||
|
||||
For more information on the database secrets engine's HTTP API please see the
|
||||
[Database secrets engine API](/api/secret/databases) page.
|
||||
[Database secrets engine API](/api-docs/secret/databases) page.
|
||||
|
|
|
|||
|
|
@ -223,4 +223,4 @@ Refer to the following step-by-step tutorials for more information:
|
|||
## API
|
||||
|
||||
The database secrets engine has a full HTTP API. Please see the [Database secret
|
||||
secrets engine API](/api/secret/databases) for more details.
|
||||
secrets engine API](/api-docs/secret/databases) for more details.
|
||||
|
|
|
|||
|
|
@ -80,7 +80,7 @@ the proper permission, it can generate credentials.
|
|||
## API
|
||||
|
||||
The full list of configurable options can be seen in the [InfluxDB database
|
||||
plugin API](/api/secret/databases/influxdb) page.
|
||||
plugin API](/api-docs/secret/databases/influxdb) page.
|
||||
|
||||
For more information on the database secrets engine's HTTP API please see the [Database secret
|
||||
secrets engine API](/api/secret/databases) page.
|
||||
secrets engine API](/api-docs/secret/databases) page.
|
||||
|
|
|
|||
|
|
@ -107,7 +107,7 @@ step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The full list of configurable options can be seen in the [MongoDB database
|
||||
plugin API](/api/secret/databases/mongodb) page.
|
||||
plugin API](/api-docs/secret/databases/mongodb) page.
|
||||
|
||||
For more information on the database secrets engine's HTTP API please see the
|
||||
[Database secrets engine API](/api/secret/databases) page.
|
||||
[Database secrets engine API](/api-docs/secret/databases) page.
|
||||
|
|
|
|||
|
|
@ -81,4 +81,4 @@ The full list of configurable options can be seen in the [MongoDB Atlas Database
|
|||
Plugin HTTP API](/api-docs/secret/databases/mongodbatlas) page.
|
||||
|
||||
For more information on the database secrets engine's HTTP API please see the
|
||||
[Database Secrets Engine API](/api/secret/databases) page.
|
||||
[Database Secrets Engine API](/api-docs/secret/databases) page.
|
||||
|
|
|
|||
|
|
@ -165,7 +165,7 @@ vault write database/roles/my-role revocation_statements="\
|
|||
## API
|
||||
|
||||
The full list of configurable options can be seen in the [MSSQL database
|
||||
plugin API](/api/secret/databases/mssql) page.
|
||||
plugin API](/api-docs/secret/databases/mssql) page.
|
||||
|
||||
For more information on the database secrets engine's HTTP API please see the
|
||||
[Database secrets engine API](/api/secret/databases) page.
|
||||
[Database secrets engine API](/api-docs/secret/databases) page.
|
||||
|
|
|
|||
|
|
@ -141,7 +141,7 @@ $ vault write database/roles/my-role \
|
|||
|
||||
The default root rotation setup for MySQL uses the `ALTER USER` syntax present
|
||||
in MySQL 5.7 and up. For MySQL 5.6, the [root rotation
|
||||
statements](/api/secret/databases#root_rotation_statements)
|
||||
statements](/api-docs/secret/databases#root_rotation_statements)
|
||||
must be configured to use the old `SET PASSWORD` syntax. For example:
|
||||
|
||||
```shell-session
|
||||
|
|
@ -160,7 +160,7 @@ Rotation](/guides/secret-mgmt/db-root-rotation).
|
|||
## API
|
||||
|
||||
The full list of configurable options can be seen in the [MySQL database plugin
|
||||
API](/api/secret/databases/mysql-maria) page.
|
||||
API](/api-docs/secret/databases/mysql-maria) page.
|
||||
|
||||
For more information on the database secrets engine's HTTP API please see the
|
||||
[Database secrets engine API](/api/secret/databases) page.
|
||||
[Database secrets engine API](/api-docs/secret/databases) page.
|
||||
|
|
|
|||
|
|
@ -232,7 +232,7 @@ the proper permission, it can generate credentials.
|
|||
## API
|
||||
|
||||
The full list of configurable options can be seen in the [Oracle database plugin
|
||||
API](/api/secret/databases/oracle) page.
|
||||
API](/api-docs/secret/databases/oracle) page.
|
||||
|
||||
For more information on the database secrets engine's HTTP API please see the
|
||||
[Database secrets engine API](/api/secret/databases) page.
|
||||
[Database secrets engine API](/api-docs/secret/databases) page.
|
||||
|
|
|
|||
|
|
@ -88,7 +88,7 @@ the proper permission, it can generate credentials.
|
|||
## API
|
||||
|
||||
The full list of configurable options can be seen in the [PostgreSQL database
|
||||
plugin API](/api/secret/databases/postgresql) page.
|
||||
plugin API](/api-docs/secret/databases/postgresql) page.
|
||||
|
||||
For more information on the database secrets engine's HTTP API please see the
|
||||
[Database secrets engine API](/api/secret/databases) page.
|
||||
[Database secrets engine API](/api-docs/secret/databases) page.
|
||||
|
|
|
|||
|
|
@ -81,7 +81,7 @@ the proper permission, it can generate credentials.
|
|||
## API
|
||||
|
||||
The full list of configurable options can be seen in the [Redshift database
|
||||
plugin API](/api/secret/databases/redshift) page.
|
||||
plugin API](/api-docs/secret/databases/redshift) page.
|
||||
|
||||
For more information on the database secrets engine's HTTP API please see the
|
||||
[Database secrets engine API](/api/secret/databases) page.
|
||||
[Database secrets engine API](/api-docs/secret/databases) page.
|
||||
|
|
|
|||
|
|
@ -105,7 +105,7 @@ the proper permission, it can generate credentials.
|
|||
## API
|
||||
|
||||
The full list of configurable options can be seen in the [Snowflake database
|
||||
plugin API](/api/secret/databases/snowflake) page.
|
||||
plugin API](/api-docs/secret/databases/snowflake) page.
|
||||
|
||||
For more information on the database secrets engine's HTTP API please see the
|
||||
[Database secrets engine API](/api/secret/databases) page.
|
||||
[Database secrets engine API](/api-docs/secret/databases) page.
|
||||
|
|
|
|||
|
|
@ -500,7 +500,7 @@ You can either:
|
|||
If the mount is configured with credentials directly, the credential's key may be
|
||||
rotated to a Vault-generated value that is not accessible by the operator. For more
|
||||
details on this operation, please see the
|
||||
[Root Credential Rotation](/api/secret/gcp#rotate-root-credentials) API docs.
|
||||
[Root Credential Rotation](/api-docs/secret/gcp#rotate-root-credentials) API docs.
|
||||
|
||||
## Things to Note
|
||||
|
||||
|
|
@ -630,7 +630,7 @@ Please report issues, add feature requests, and submit contributions to the
|
|||
The GCP secrets engine has a full HTTP API. Please see the [GCP secrets engine API docs][api]
|
||||
for more details.
|
||||
|
||||
[api]: /api/secret/gcp
|
||||
[api]: /api-docs/secret/gcp
|
||||
[cloud-creds]: https://cloud.google.com/docs/authentication/production#providing_credentials_to_your_application
|
||||
[custom-roles]: https://cloud.google.com/iam/docs/creating-custom-roles
|
||||
[gce]: https://cloud.google.com/compute/
|
||||
|
|
|
|||
|
|
@ -435,7 +435,7 @@ Please report issues, add feature requests, and submit contributions to the
|
|||
The Google Cloud KMS secrets engine has a full HTTP API. Please see the
|
||||
[Google Cloud KMS secrets engine API docs][api] for more details.
|
||||
|
||||
[api]: /api/secret/gcpkms
|
||||
[api]: /api-docs/secret/gcpkms
|
||||
[cloud-creds]: https://cloud.google.com/docs/authentication/production#providing_credentials_to_your_application
|
||||
[gce]: https://cloud.google.com/compute/
|
||||
[gke]: https://cloud.google.com/kubernetes-engine/
|
||||
|
|
|
|||
|
|
@ -143,7 +143,7 @@ The full list of template parameters is shown below:
|
|||
### Token Generation
|
||||
|
||||
An authenticated client may request a token using the [token generation
|
||||
endpoint](/api/secret/identity/tokens#generate-a-signed-id-token). The token
|
||||
endpoint](/api-docs/secret/identity/tokens#generate-a-signed-id-token). The token
|
||||
will be generated per the requested role's specifications, for the requester's
|
||||
entity. It is not possible to generate tokens for an arbitrary entity.
|
||||
|
||||
|
|
@ -161,7 +161,7 @@ only requiring _access_ to Vault, not _authorization_, as the .well-known
|
|||
endpoints are unauthenticated.
|
||||
|
||||
Alternatively, the token may be sent to Vault for verification via an
|
||||
[introspection endpoint](/api/secret/identity/tokens#introspect-a-signed-id-token).
|
||||
[introspection endpoint](/api-docs/secret/identity/tokens#introspect-a-signed-id-token).
|
||||
The response will indicate whether the token is "active" or not, as well as any
|
||||
errors that occurred during validation. Beyond simply allowing the client to
|
||||
delegate verification to Vault, using this endpoint incorporates the additional
|
||||
|
|
@ -183,7 +183,7 @@ an issuer that must match the request.
|
|||
By default Vault will set the issuer to the Vault instance's
|
||||
[`api_addr`](/docs/configuration#api_addr). This means that tokens
|
||||
issued in a given cluster should be validated within that same cluster.
|
||||
Alternatively, the [`issuer`](/api/secret/identity/tokens#issuer) parameter
|
||||
Alternatively, the [`issuer`](/api-docs/secret/identity/tokens#issuer) parameter
|
||||
may be configured explicitly. This address must point to the identity/oidc path
|
||||
for the Vault instance (e.g.
|
||||
`https://vault-1.example.com:8200/v1/identity/oidc`) and should be
|
||||
|
|
@ -192,5 +192,5 @@ reachable by any client trying to validate identity tokens.
|
|||
## API
|
||||
|
||||
The Identity secrets engine has a full HTTP API. Please see the
|
||||
[Identity secrets engine API](/api/secret/identity) for more
|
||||
[Identity secrets engine API](/api-docs/secret/identity) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -42,7 +42,7 @@ one is individually documented on its own page.
|
|||
## API
|
||||
|
||||
The Identity secrets engine has a full HTTP API. Please see the
|
||||
[Identity secrets engine API](/api/secret/identity) for more
|
||||
[Identity secrets engine API](/api-docs/secret/identity) for more
|
||||
details.
|
||||
|
||||
Additionally, Vault can be configured as an OIDC identity provider. Please see
|
||||
|
|
|
|||
|
|
@ -20,11 +20,11 @@ the functionality.
|
|||
|
||||
The Key Management secrets engine must be configured with credentials that have sufficient
|
||||
permissions to manage keys in an AWS KMS region. The authentication parameters are described
|
||||
in the [credentials](/api/secret/key-management/awskms#credentials) section of the API
|
||||
in the [credentials](/api-docs/secret/key-management/awskms#credentials) section of the API
|
||||
documentation. The authentication parameters will be set with the following order of
|
||||
precedence:
|
||||
|
||||
1. [KMS provider credentials](/api/secret/key-management/awskms#credentials)
|
||||
1. [KMS provider credentials](/api-docs/secret/key-management/awskms#credentials)
|
||||
2. Environment variables
|
||||
3. Shared credentials file
|
||||
4. IAM role for AWS EC2 or ECS task
|
||||
|
|
@ -56,7 +56,7 @@ $ vault write keymgmt/kms/example-kms \
|
|||
credentials=secret_key="bCiYmNroLxLmPNQ47VIvjlm8mQu5oktZcQdq195w"
|
||||
```
|
||||
|
||||
Refer to the AWS KMS [API documentation](/api/secret/key-management/awskms)
|
||||
Refer to the AWS KMS [API documentation](/api-docs/secret/key-management/awskms)
|
||||
for a detailed description of individual configuration parameters.
|
||||
|
||||
## Key Transfer Specification
|
||||
|
|
|
|||
|
|
@ -18,12 +18,12 @@ the functionality.
|
|||
|
||||
The Key Management secrets engine must be configured with credentials that have sufficient
|
||||
permissions to manage keys in an Azure Key Vault instance. The authentication parameters are
|
||||
described in the [credentials](/api/secret/key-management/azurekeyvault#credentials) section
|
||||
described in the [credentials](/api-docs/secret/key-management/azurekeyvault#credentials) section
|
||||
of the API documentation. The authentication parameters will be set with the following order
|
||||
of precedence:
|
||||
|
||||
1. Environment variables
|
||||
2. [KMS provider credentials](/api/secret/key-management/azurekeyvault#credentials)
|
||||
2. [KMS provider credentials](/api-docs/secret/key-management/azurekeyvault#credentials)
|
||||
3. [Managed Service Identity (MSI)](https://docs.microsoft.com/en-us/azure/active-directory/managed-service-identity/overview)
|
||||
|
||||
If the client ID or secret are not provided and Vault is running on an Azure VM, Vault will attempt
|
||||
|
|
@ -54,7 +54,7 @@ $ vault write keymgmt/kms/example-kms \
|
|||
credentials=tenant_id="cd4bf224-d114-4f96-9bbc-b8f45751c43f"
|
||||
```
|
||||
|
||||
Refer to the Azure Key Vault [API documentation](/api/secret/key-management/azurekeyvault)
|
||||
Refer to the Azure Key Vault [API documentation](/api-docs/secret/key-management/azurekeyvault)
|
||||
for a detailed description of individual configuration parameters.
|
||||
|
||||
## Key Transfer Specification
|
||||
|
|
|
|||
|
|
@ -18,12 +18,12 @@ the functionality.
|
|||
|
||||
The Key Management secrets engine must be configured with credentials that have sufficient
|
||||
permissions to manage keys in an existing GCP Cloud KMS [key ring](https://cloud.google.com/kms/docs/resource-hierarchy#key_rings).
|
||||
The authentication parameters are described in the [credentials](/api/secret/key-management/gcpkms#credentials)
|
||||
The authentication parameters are described in the [credentials](/api-docs/secret/key-management/gcpkms#credentials)
|
||||
section of the API documentation. The authentication parameters will be set with the following order
|
||||
of precedence:
|
||||
|
||||
1. `GOOGLE_CREDENTIALS` environment variable
|
||||
2. [KMS provider credentials](/api/secret/key-management/gcpkms#credentials) parameter
|
||||
2. [KMS provider credentials](/api-docs/secret/key-management/gcpkms#credentials) parameter
|
||||
3. [Application default credentials](https://cloud.google.com/docs/authentication/production)
|
||||
|
||||
The service account must be authorized with the following minimum
|
||||
|
|
@ -50,7 +50,7 @@ $ vault write keymgmt/kms/example-kms \
|
|||
credentials=service_account_file="/path/to/service_account/credentials.json"
|
||||
```
|
||||
|
||||
Refer to the GCP Cloud KMS [API documentation](/api/secret/key-management/gcpkms)
|
||||
Refer to the GCP Cloud KMS [API documentation](/api-docs/secret/key-management/gcpkms)
|
||||
for a detailed description of individual configuration parameters.
|
||||
|
||||
## Key Transfer Specification
|
||||
|
|
|
|||
|
|
@ -89,7 +89,7 @@ manage the lifecycle of cryptographic keys in [supported KMS providers](#kms-pro
|
|||
`purpose` and `protection`. The `purpose` defines the set of cryptographic capabilities
|
||||
that the key will have in the KMS provider. The `protection` defines where cryptographic
|
||||
operations are performed with the key in the KMS provider. See the API documentation for a list of
|
||||
supported [purpose](/api/secret/key-management#purpose) and [protection](/api/secret/key-management#protection)
|
||||
supported [purpose](/api-docs/secret/key-management#purpose) and [protection](/api-docs/secret/key-management#protection)
|
||||
values.
|
||||
|
||||
~> **Note:** The amount of time it takes to distribute a key to a KMS provider is proportional to the
|
||||
|
|
@ -126,7 +126,7 @@ manage the lifecycle of cryptographic keys in [supported KMS providers](#kms-pro
|
|||
This operation results in the key being deleted from the KMS provider. The key will still exist
|
||||
in the secrets engine and can be redistributed to a KMS provider at a later time.
|
||||
|
||||
To permanently delete the key from the secrets engine, the [delete key](/api/secret/key-management#delete-key)
|
||||
To permanently delete the key from the secrets engine, the [delete key](/api-docs/secret/key-management#delete-key)
|
||||
API may be invoked.
|
||||
|
||||
## Key Types
|
||||
|
|
@ -174,5 +174,5 @@ a step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The Key Management secrets engine has a full HTTP API. Please see the
|
||||
[Key Management Secrets Engine API](/api/secret/key-management) for more
|
||||
[Key Management Secrets Engine API](/api-docs/secret/key-management) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -107,5 +107,5 @@ guide for a step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The KV secrets engine has a full HTTP API. Please see the
|
||||
[KV secrets engine API](/api/secret/kv/kv-v1) for more
|
||||
[KV secrets engine API](/api-docs/secret/kv/kv-v1) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -156,7 +156,7 @@ The `allowed_parameters`, `denied_parameters`, and `required_parameters` fields
|
|||
not supported for policies used with the version 2 kv store. See the [Policies Concepts](/docs/concepts/policies)
|
||||
for a description of these parameters.
|
||||
|
||||
See the [API Specification](/api/secret/kv/kv-v2) for more
|
||||
See the [API Specification](/api-docs/secret/kv/kv-v2) for more
|
||||
information.
|
||||
|
||||
## Usage
|
||||
|
|
@ -543,5 +543,5 @@ guide for a step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The KV secrets engine has a full HTTP API. Please see the
|
||||
[KV secrets engine API](/api/secret/kv/kv-v2) for more
|
||||
[KV secrets engine API](/api-docs/secret/kv/kv-v2) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -14,7 +14,7 @@ time-based and are automatically revoked when the Vault lease expires, unless re
|
|||
Vault will create a Programmatic API key for each lease that provide appropriate access to the defined MongoDB Atlas
|
||||
project or organization with appropriate role(s). The MongoDB Atlas Programmatic API Key Public and
|
||||
Private Keys are returned to the caller. To learn more about Programmatic API Keys visit the
|
||||
[Programmatic API Keys Doc](https://docs.atlas.mongodb.com/reference/api/apiKeys/).
|
||||
[Programmatic API Keys Doc](https://docs.atlas.mongodb.com/reference/api-docs/apiKeys/).
|
||||
|
||||
## Setup
|
||||
|
||||
|
|
@ -35,7 +35,7 @@ steps are usually completed by an operator or configuration management tool.
|
|||
or project that has sufficient permissions to allow Vault to create other Programmatic API Keys.
|
||||
|
||||
In order to grant Vault programmatic access to an organization or project using only the
|
||||
[API](https://docs.atlas.mongodb.com/api/) you need to create a MongoDB Atlas Programmatic API
|
||||
[API](https://docs.atlas.mongodb.com/api-docs/) you need to create a MongoDB Atlas Programmatic API
|
||||
Key with the appropriate roles if you have not already done so. A Programmatic API Key consists
|
||||
of a public and private key, so ensure you have both. Regarding roles, the Organization Owner and
|
||||
Project Owner roles should be sufficient for most needs, however be sure to check what each role
|
||||
|
|
@ -104,7 +104,7 @@ $ vault write mongodbatlas/roles/test \
|
|||
|
||||
~> **Note:** MongoDB Atlas has deprecated whitelists, and the API will be disabled in June 2021. It is replaced by a
|
||||
similar access list API which is live now. If you specify CIDR blocks or IP addresses to allow, you need to run **Vault
|
||||
1.6.3 or greater** to avoid interruption. See [MongoDB Atlas documentation](https://docs.atlas.mongodb.com/reference/api/access-lists/)
|
||||
1.6.3 or greater** to avoid interruption. See [MongoDB Atlas documentation](https://docs.atlas.mongodb.com/reference/api-docs/access-lists/)
|
||||
for further details.
|
||||
|
||||
Programmatic API Key access can and should be limited with a IP Network Access list. In the following example both a CIDR
|
||||
|
|
@ -188,4 +188,4 @@ $ vault read mongodbatlas/creds/test
|
|||
## API
|
||||
|
||||
The MongoDB Atlas secrets engine has a full HTTP API. Please see the
|
||||
[MongoDB Atlas secrets engine API docs](/api/secret/mongodbatlas) for more details.
|
||||
[MongoDB Atlas secrets engine API docs](/api-docs/secret/mongodbatlas) for more details.
|
||||
|
|
|
|||
|
|
@ -119,5 +119,5 @@ step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The Nomad secret backend has a full HTTP API. Please see the
|
||||
[Nomad secret backend API](/api/secret/nomad) for more
|
||||
[Nomad secret backend API](/api-docs/secret/nomad) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -693,5 +693,5 @@ guide for a step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The PKI secrets engine has a full HTTP API. Please see the
|
||||
[PKI secrets engine API](/api/secret/pki) for more
|
||||
[PKI secrets engine API](/api-docs/secret/pki) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -94,7 +94,7 @@ the proper permission, it can generate credentials.
|
|||
## API
|
||||
|
||||
The RabbitMQ secrets engine has a full HTTP API. Please see the
|
||||
[RabbitMQ secrets engine API](/api/secret/rabbitmq) for more
|
||||
[RabbitMQ secrets engine API](/api-docs/secret/rabbitmq) for more
|
||||
details.
|
||||
|
||||
[rmq-perms]: https://www.rabbitmq.com/management.html#permissions
|
||||
|
|
|
|||
|
|
@ -189,5 +189,5 @@ username@<IP of remote host>:~$
|
|||
## API
|
||||
|
||||
The SSH secret secrets engine has a full HTTP API. Please see the
|
||||
[SSH secret secrets engine API](/api/secret/ssh) for more
|
||||
[SSH secret secrets engine API](/api-docs/secret/ssh) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -29,5 +29,5 @@ All guides assume a basic familiarity with the SSH protocol.
|
|||
## API
|
||||
|
||||
The SSH secrets engine has a full HTTP API. Please see the
|
||||
[SSH secrets engine API](/api/secret/ssh) for more
|
||||
[SSH secrets engine API](/api-docs/secret/ssh) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -116,5 +116,5 @@ for a step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The SSH secrets engine has a full HTTP API. Please see the
|
||||
[SSH secrets engine API](/api/secret/ssh) for more
|
||||
[SSH secrets engine API](/api-docs/secret/ssh) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -505,5 +505,5 @@ forwarding. See [no prompt after login](#no-prompt-after-login) for examples.
|
|||
## API
|
||||
|
||||
The SSH secrets engine has a full HTTP API. Please see the
|
||||
[SSH secrets engine API](/api/secret/ssh) for more
|
||||
[SSH secrets engine API](/api-docs/secret/ssh) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -55,7 +55,7 @@ management tool.
|
|||
and manages the lifecycle of that API token. You will need to know the User
|
||||
ID in order to generate User API tokens for that user. You can use the
|
||||
Terraform Cloud [Account
|
||||
API](https://www.terraform.io/docs/cloud/api/account.html) to find the
|
||||
API](https://www.terraform.io/docs/cloud/api-docs/account.html) to find the
|
||||
desired User ID.
|
||||
|
||||
```shell-session
|
||||
|
|
@ -167,5 +167,5 @@ for a step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The Terraform Cloud secrets engine has a full HTTP API. Please see the
|
||||
[Terraform Cloud secrets engine API](/api/secret/terraform) for more
|
||||
[Terraform Cloud secrets engine API](/api-docs/secret/terraform) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -120,5 +120,5 @@ management tool.
|
|||
## API
|
||||
|
||||
The TOTP secrets engine has a full HTTP API. Please see the
|
||||
[TOTP secrets engine API](/api/secret/totp) for more
|
||||
[TOTP secrets engine API](/api-docs/secret/totp) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -346,5 +346,5 @@ Refer to the [Transform Secrets Engine](https://learn.hashicorp.com/vault/adp/tr
|
|||
## API
|
||||
|
||||
The Transform secrets engine has a full HTTP API. Please see the
|
||||
[Transform secrets engine API](/api/secret/transform) for more
|
||||
[Transform secrets engine API](/api-docs/secret/transform) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -241,5 +241,5 @@ guide for a step-by-step tutorial.
|
|||
## API
|
||||
|
||||
The Transit secrets engine has a full HTTP API. Please see the
|
||||
[Transit secrets engine API](/api/secret/transit) for more
|
||||
[Transit secrets engine API](/api-docs/secret/transit) for more
|
||||
details.
|
||||
|
|
|
|||
|
|
@ -300,6 +300,6 @@ To see all of the options available when requesting a certificate, including
|
|||
## API
|
||||
|
||||
Venafi Machine Identity Secrets Engine uses the same
|
||||
[Vault API](/api/secret/pki)
|
||||
[Vault API](/api-docs/secret/pki)
|
||||
as the built-in PKI secrets engine. Some methods, such as those for
|
||||
managing certificate authorities, do not apply.
|
||||
|
|
|
|||
|
|
@ -38,4 +38,4 @@ instance or through a load balancer can result in mismatched
|
|||
plugin binaries within a cluster. On a replicated cluster this may be accomplished
|
||||
by setting the 'scope' parameter of the reload to 'global'.
|
||||
|
||||
[plugin_reload_api]: /api/system/plugins-reload-backend
|
||||
[plugin_reload_api]: /api-docs/system/plugins-reload-backend
|
||||
|
|
|
|||
|
|
@ -15,9 +15,9 @@ for Vault 0.10.2 compared to 0.10.1. Please read it carefully.
|
|||
|
||||
If you are using `transit`'s convergent encryption feature, which prior to this
|
||||
release was at version 2, we recommend
|
||||
[rotating](/api/secret/transit#rotate-key)
|
||||
[rotating](/api-docs/secret/transit#rotate-key)
|
||||
your encryption key (the new key will use version 3) and
|
||||
[rewrapping](/api/secret/transit#rewrap-data)
|
||||
[rewrapping](/api-docs/secret/transit#rewrap-data)
|
||||
your data to mitigate the chance of offline plaintext-confirmation attacks.
|
||||
|
||||
### PKI duration return types
|
||||
|
|
|
|||
|
|
@ -136,9 +136,9 @@ allowing it to be set manually didn't make sense.
|
|||
|
||||
If you are using `transit`'s convergent encryption feature, which prior to this
|
||||
release was at version 2, we recommend
|
||||
[rotating](/api/secret/transit#rotate-key)
|
||||
[rotating](/api-docs/secret/transit#rotate-key)
|
||||
your encryption key (the new key will use version 3) and
|
||||
[rewrapping](/api/secret/transit#rewrap-data)
|
||||
[rewrapping](/api-docs/secret/transit#rewrap-data)
|
||||
your data to mitigate the chance of offline plaintext-confirmation attacks.
|
||||
|
||||
### PKI duration return types
|
||||
|
|
|
|||
|
|
@ -38,7 +38,7 @@ each status code (including `500`).
|
|||
|
||||
Root tokens (tokens with the `root` policy) can no longer be created except by
|
||||
another root token or the
|
||||
[`generate-root`](/api/system/generate-root)
|
||||
[`generate-root`](/api-docs/system/generate-root)
|
||||
endpoint or CLI command.
|
||||
|
||||
## PKI Backend Certificates Will Contain Default Key Usages
|
||||
|
|
|
|||
|
|
@ -49,4 +49,4 @@ is performing an explicit reindex.
|
|||
This path was meant to require `sudo` capability but was not implemented this
|
||||
way. It now requires `sudo` capability to run.
|
||||
|
||||
[reindex]: /api/system/replication#reindex-replication
|
||||
[reindex]: /api-docs/system/replication#reindex-replication
|
||||
|
|
|
|||
|
|
@ -117,5 +117,5 @@ corresponding object containing the `key_type`.
|
|||
Audit request and response entries are still in RFC3339 format but now have a
|
||||
granularity of nanoseconds.
|
||||
|
||||
[generate-root]: /api/secret/pki#generate-root
|
||||
[generate-root]: /api-docs/secret/pki#generate-root
|
||||
[pkcs11-seal]: /docs/configuration/seal/pkcs11
|
||||
|
|
|
|||
|
|
@ -38,14 +38,14 @@ token roles. When creating a role, the key parameter is required and the key
|
|||
must exist. Previously, it was possible to create a role and assign it a named
|
||||
key that did not yet exist despite the documentation stating otherwise.
|
||||
|
||||
All calls to [create or update a role](https://www.vaultproject.io/api/secret/identity/tokens#create-or-update-a-role)
|
||||
All calls to [create or update a role](https://www.vaultproject.io/api-docs/secret/identity/tokens#create-or-update-a-role)
|
||||
must be checked to ensure that roles are not being created or updated with
|
||||
non-existent keys.
|
||||
|
||||
## SSH Role Parameter `allowed_extensions` Behavior Change
|
||||
|
||||
Prior versions of Vault allowed clients to specify any extension when requesting
|
||||
SSH certificate [signing requests](https://www.vaultproject.io/api/secret/ssh#sign-ssh-key)
|
||||
SSH certificate [signing requests](https://www.vaultproject.io/api-docs/secret/ssh#sign-ssh-key)
|
||||
if their role had an `allowed_extensions` set to `""` or was missing.
|
||||
|
||||
Now, Vault will reject a client request that specifies extensions if the role
|
||||
|
|
|
|||
Loading…
Reference in New Issue